Secure X.509 authentication is essential for your business, giving you strong identity verification and encryption for sensitive communications. It simplifies access management and boosts your cybersecurity posture, all while helping you comply with regulations. With Keytalk, you can efficiently manage X.509 certificates, automate issuance and renewals, and reduce human error. By adopting this robust security framework, you’ll foster a more secure environment. Discover how you can enhance your organization’s security even further.
Key Takeaways
- X.509 certificates act as digital passports, confirming identities and securing communications within your business. Keytalk streamlines certificate management, automating issuance and renewals to enhance security and reduce human errors. Implementing X.509 authentication simplifies user access management, minimizing password-related issues and improving efficiency. Strong encryption provided by X.509 enhances your organization's cybersecurity posture, aiding in regulatory compliance and reducing breach risks. Real-world applications show that adopting X.509 authentication fosters a secure environment, boosting trust and operational efficiency across various industries.
Understanding X.509 Certificates and Their Role in Security
 Unlock Vpn Access For Enterprises
Unlock Vpn Access For EnterprisesWhen you think about securing your business's digital communications, understanding X.509 certificates is essential.
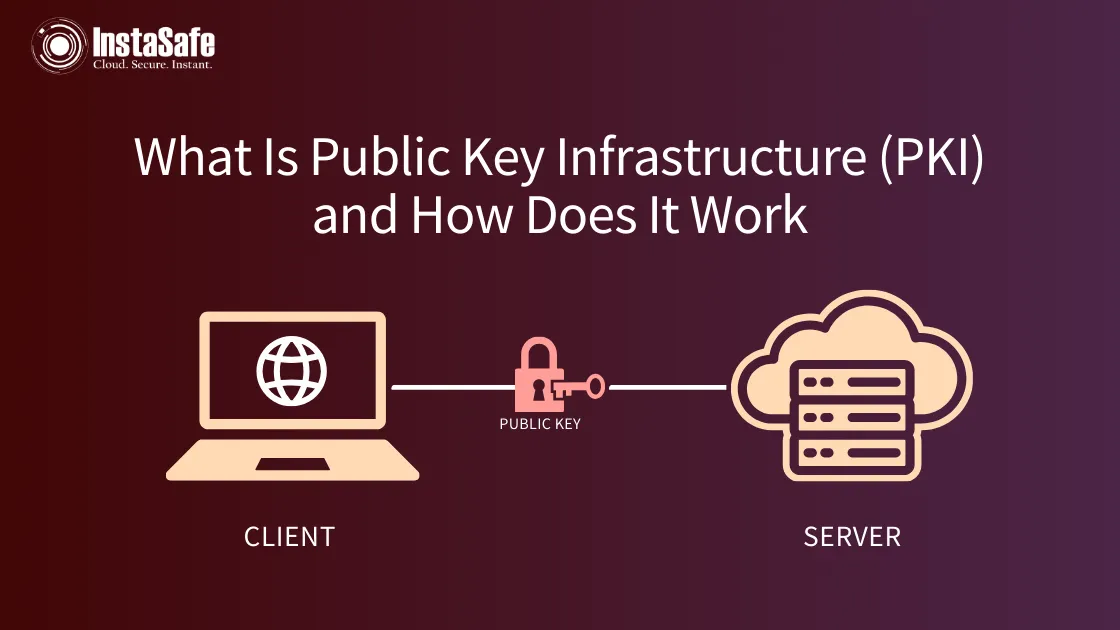
These certificates act as a digital passport for your organization, confirming the identity of users and devices. They utilize a public key infrastructure (PKI) to establish trust, ensuring that data exchanged over networks remains secure.
By encrypting communications and authenticating identities, X.509 certificates help prevent unauthorized access and data breaches. You'll find them widely used in various applications, including email security and secure web browsing (HTTPS).
X.509 certificates encrypt communications and authenticate identities, crucial for preventing unauthorized access and ensuring data security.
It's vital to implement these certificates effectively, as they not only safeguard sensitive information but also enhance your business's reputation. Knowing how they function https://passrealnews.com/s-mime-management-and-automation-keytalk/ empowers you to make informed decisions about your digital security strategies.
 Automate Semantic Ai Search The Smart Way
Automate Semantic Ai Search The Smart WayBenefits of Secure X.509 Authentication
Implementing secure X.509 authentication brings numerous advantages that can greatly enhance your business's cybersecurity posture.
Here are some key benefits you can expect:
Robust Security: X.509 certificates provide strong encryption, making it difficult for unauthorized users to access sensitive information. Authentication Assurance: They verify the identity of users and devices, ensuring that only trusted entities can interact with your systems. Streamlined Access Management: With digital certificates, you can simplify user access and control, reducing the burden of password management. Regulatory Compliance: Using X.509 authentication helps meet industry standards and regulations, protecting your business from potential fines and reputational damage.How Keytalk Enhances Your Security Framework
As businesses increasingly rely on digital interactions, integrating Keytalk into your security framework can markedly bolster your defenses.
Keytalk streamlines the management of X.509 certificates, enhancing your identity verification processes. With its robust encryption capabilities, you can safeguard sensitive data and guarantee secure communication between users and devices.
 Master Key Management System For Enterprises
Master Key Management System For EnterprisesAdditionally, Keytalk simplifies the deployment of certificates, reducing the risk of human error. By automating certificate issuance and renewals, you maintain continuous security without manual intervention. This proactive approach not only enhances security but also boosts operational efficiency.
Ultimately, embracing Keytalk enables you to create a more resilient security posture, empowering your organization to thrive in today’s digital landscape while protecting against emerging threats.
Implementing Secure X.509 Authentication in Your Organization
To guarantee your organization reaps the full benefits of X.509 authentication, it's crucial to adopt a structured approach to implementation.
Adopting a structured approach to X.509 authentication is essential for maximizing your organization's security benefits.
Start by evaluating your current security framework and identifying areas for improvement.
Here are four key steps to follow:
Choose a Certificate Authority (CA): Select a reliable CA to issue your X.509 certificates, ensuring trustworthiness. Deploy a PKI System: Implement a Public Key Infrastructure to manage certificates and keys securely. Establish Policies: Create clear guidelines for certificate issuance, renewal, and revocation to maintain security standards. Train Employees: Educate your team about the importance of X.509 authentication and best practices for using certificates effectively.Real-World Applications and Success Stories
What can you learn from organizations that have successfully implemented X.509 authentication? These businesses have seen remarkable improvements in security and efficiency.
For instance, a leading healthcare provider adopted X.509 certificates to protect patient data, reducing breaches considerably.
Another tech company streamlined its login processes, enabling employees to access resources securely without compromising sensitive information.
A financial institution utilized X.509 authentication to enhance its online transactions, building customer trust and increasing user satisfaction.
By learning from these success stories, you can understand the real-world benefits of adopting X.509 authentication.
It’s not just about compliance; it’s about creating a secure environment that fosters growth and innovation in your organization.
Embrace the change, and watch your security posture strengthen.
Frequently Asked Questions
What Types of Businesses Benefit Most From X.509 Authentication?
X.509 authentication is vital for businesses that prioritize security and data integrity, especially in sectors like finance, healthcare, and technology.
If you handle sensitive information or require secure transactions, you'll find it indispensable. Companies with remote employees or those that use cloud services also benefit greatly, as X.509 certificates help guarantee secure communications.
Are There Any Costs Associated With Implementing X.509 Certificates?
When it comes to implementing X.509 certificates, think of it as an investment in your business’s security rather than a cost.
You’ll encounter expenses like certificate authority fees, hardware requirements, and possibly training for your staff. However, these costs are often outweighed by the peace of mind and protection you gain.
How Long Do X.509 Certificates Typically Last Before Renewal?
X.509 certificates typically last one to three years before you need to renew them.
The exact duration depends on the certificate authority you choose.
It’s important to keep track of expiration dates, as failing to renew on time can disrupt services and compromise security.
Setting reminders a few months in advance can help guarantee you’re prepared for renewal and maintain the integrity of your communications and transactions.
Can X.509 Certificates Be Used for Mobile Devices?
Absolutely, you can use X.509 certificates for mobile devices!
Just like how folks used to send telegrams, these certificates help secure your communications. They authenticate users and devices, guaranteeing that only authorized entities access your services.
Mobile apps can leverage these certificates for secure connections, enhancing data privacy. Just verify that your mobile platform supports the certificate management you need, and you’ll be all set to improve your security on the go!
What Happens if a Certificate Is Compromised?
If a certificate gets compromised, you’re facing significant risks.
An attacker can impersonate your identity, access sensitive data, or launch man-in-the-middle attacks. You need to act quickly—revoke the compromised certificate, notify affected parties, and issue a new one.
Regular audits and monitoring can help you spot vulnerabilities early.
Don't forget to educate your team on best practices for handling certificates to minimize the chances of future compromises.
Conclusion
In today’s digital landscape, embracing secure X.509 authentication isn’t just a smart move—it’s a savvy strategy for safeguarding your business. With Keytalk by your side, you’re not only bolstering your security framework but also ensuring peace of mind. So, why not take the leap? By implementing these robust solutions, you're not just keeping threats at bay; you’re paving the way for a safer, more secure future for your organization. Let’s secure your digital world together!